What the hell is SASE?
Cutting Through the Fog of Network Security Marketing
You Google SASE, and you'll find millions of results. You check major SASE vendors' websites. You even ask your favorite GenAI; all you see is a bunch of flowery stuff without answering the question.
So, what exactly is SASE?
SASE is a collection of, mainly, security products that you've been using for years on-prem in someone else's data center, aka cloud. They are all glued together as a single concoction called SASE!
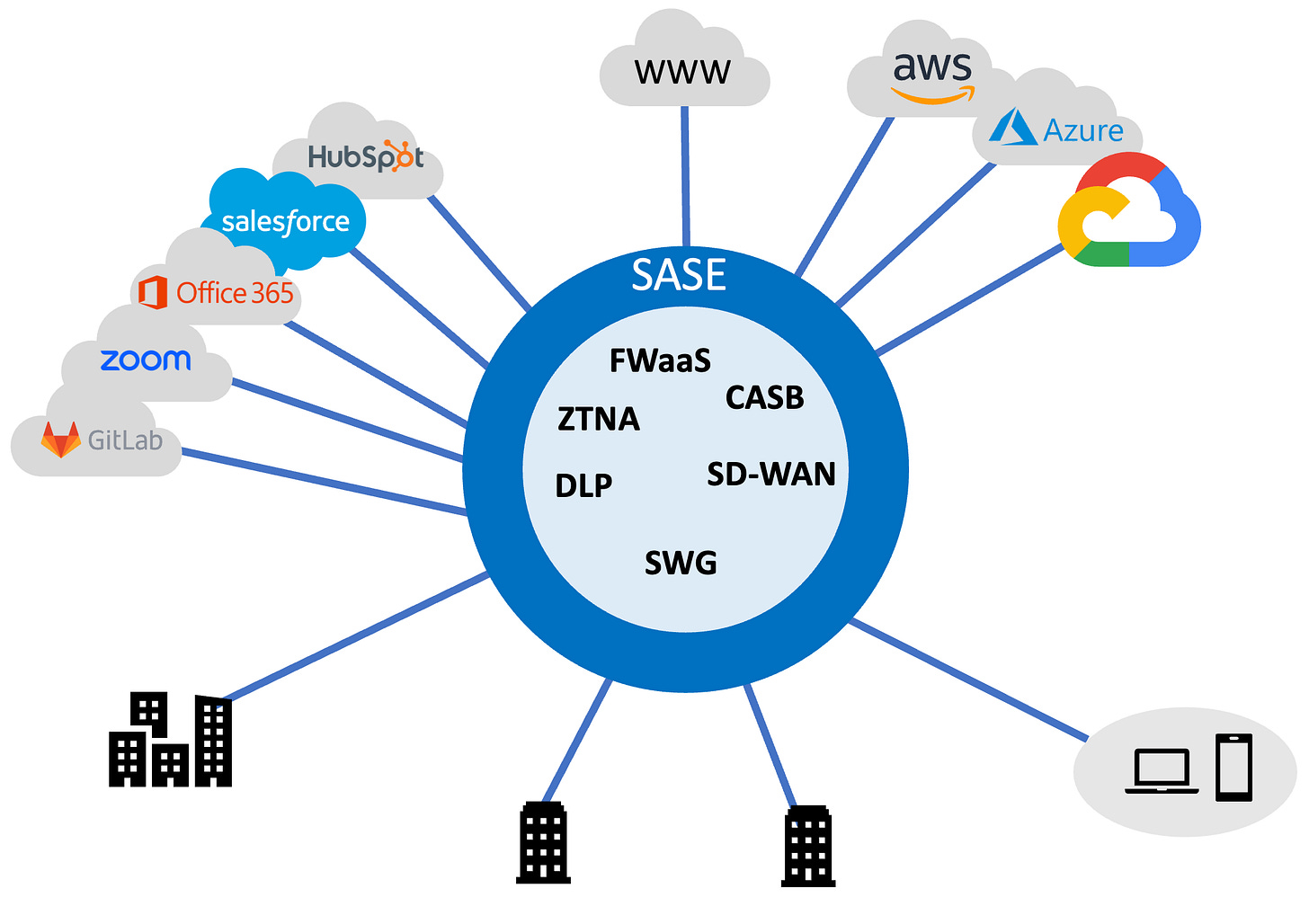
SASE then connects to everything you have, like a central hub: remote users, branch offices, on-premises data centers, cloud providers (AWS, Azure, etc.), and SaaS applications (HubSpot, Salesforce, Zoom, Github, Gitlab, etc.) – giving you full visibility and control over your entire ecosystem
That's really it!
SASE components fall into three categories:
Security: Packed with essential and not-so-essential security products: Firewall as a Service (FaaW), Secure Web Gateway (a fancy name for explicit proxy), ZTNA (elaborated, usually-always-on VPN), Data Loss Prevention, and countless others.
Network: SD-WAN is the central piece. SD-WAS allows you to abstract away the underlying WAN infrastructure—normally Internet and/or MPLS. SD-WAN has been evolving over the years.
Digital Experience Monitoring: This allows you to monitor your network performance and troubleshoot network issues, especially the ones reported by your remote users.
Why SASE Actually Matters
SASE solves real problems for distributed organizations:
Simplifies security management across multiple locations and remote users
Reduces hardware footprint in branch offices
Centralizes policy enforcement regardless of where users connect from
Potentially lowers operational costs (though vendors won't advertise if it doesn't)
Implementation Considerations
Before jumping on the SASE bandwagon, consider:
Existing security investments - what can you leverage versus replace?
Vendor lock-in risks - many SASE solutions aren't designed for interoperability
Compliance requirements - where is your data being processed?
Performance needs - latency might become critical with cloud-delivered security
Common SASE Misconceptions
Let's cut through the marketing jargon:
SASE isn't new technology - it's repackaging with better integration
It won't magically fix poor security practices
You don't need every component to benefit
The "single pane of glass" promise often requires significant configuration
Getting Started with SASE
Audit your current security and networking tools
Identify your biggest pain points (remote access? branch connectivity?)
Start with core components that address those specific challenges
Demand proof-of-concepts before committing to full implementation
Plan for coexistence with existing infrastructure during the transition
Who Benefits Most from SASE?
Organizations with many remote workers and distributed offices
Companies rapidly migrating to cloud and SaaS applications
IT teams struggling with managing multiple security products
Businesses looking to reduce on-premises hardware footprint
At SafeMesh, we understand the challenges of implementing effective network security solutions in today's distributed environments. Our approach focuses on practical, no-nonsense security implementations that deliver real value rather than just following industry buzzwords.